Thursday, August 21st, 2025
Types of Social Engineering Attacks


In the 2002 film Catch Me If You Can, Frank Abagnale Jr, played by Leonardo DiCaprio, confidently walks through an airport with a crew, posing as a Pan Am pilot despite never having seen the inside of a cockpit. With the right uniform, some jargon, and the confidence to match, he bypasses security and travels freely across the country. This is social engineering at its core: exploiting human trust and assumptions to gain access to a system.
How Can Social Engineering Exploit a Target?
Social engineering is one of the most prevalent attack vectors. Effective attack surface management must address the human factor. Organisations that neglect security awareness are more vulnerable to threats. Common techniques exploit principles such as obligation, fear of missing out, trust, commitment, kindness, and consensus.

Obligation

Attackers exploit obligation by doing a small favour first, creating pressure for victims to reciprocate or accept help in return.

Fear of Missing Out

Attackers use urgency, warning victims they’ll lose access or opportunities unless they act quickly, often without thinking critically.

Trust

By impersonating authority figures or vendors, attackers use uniforms, titles, and jargon to gain trust and lower victim defences.
Commitment

Once victims agree to small requests, attackers escalate to riskier demands, exploiting the human tendency to remain consistent and committed.

Kindness

Attackers build rapport, show empathy, or appear likeable so victims feel safe and willingly share information or provide assistance.
Consensus

In uncertain situations, attackers exploit group behaviour, claiming everyone else has complied, pressuring victims to follow perceived majority actions.
The Primary Social Engineering Attack Types
Social engineering can be classified into several attack vectors, each exploiting a specific human weakness or bias.
Phishing, Spear-Phishing, Whaling, Vishing & Smishing
Phishing attacks impersonate reputable organisations or individuals. With the rise of generative AI, these messages can be highly convincing. According to industry reports, 74% of breaches involve the human element, and Business Email Compromise (BEC) has nearly doubled, now accounting for over 50% of social engineering incidents.
Typical phishing campaigns target large numbers of businesses, flooding inboxes with generic requests. Many contain links to malicious landing pages where victims are prompted to enter sensitive details such as usernames, passwords, or bank information which enables credential theft, account compromise, and potential financial fraud.
Spear-phishing targets specific individuals, often those with access to privileged information. When high-level executives are targeted, the attack is called whaling and can result in high-value data breaches or significant financial losses.
Vishing uses similar tactics but delivered via phone calls or voice messages, while smishing applies them through SMS text messages sent to the victim’s mobile device.
Stopping phishing before it works
Smarttech247’s NoPhish solution enables employees to report suspicious emails with a single click in Office 365. Once reported, the system automatically scans the email using threat intelligence APIs, flags malicious URLs or attachments, and sends the findings to expert analysts for review. This ensures faster detection, quicker response, and reduced risk of a successful attack. With 24/7 monitoring, rapid incident management, and human-led analysis, organisations can turn their workforce into the first line of defence.
Stopping phishing before it works
Smarttech247’s NoPhish solution enables employees to report suspicious emails with a single click in Office 365. Once reported, the system automatically scans the email using threat intelligence APIs, flags malicious URLs or attachments, and sends the findings to expert analysts for review.
This ensures faster detection, quicker response, and reduced risk of a successful attack. With 24/7 monitoring, rapid incident management, and human-led analysis, organisations can turn their workforce into the first line of defence.
Pretexting
An attacker creates a false scenario to persuade a victim to disclose valuable information. Often, the attacker claims the victim has suffered a security breach and offers a “solution,” such as installing a software patch that actually contains malware.
Impersonation
The attacker poses as another person to gain system access, using props, credentials, technical jargon, or uniforms to make the deception credible.
Baiting
The attacker promises a reward in exchange for sensitive information. In most cases, the reward is never delivered.
Quid-pro-quo
Similar to baiting but involving an actual exchange of goods or services for information. The victim willingly provides details in return for the promised benefit.
Water-holing
The attacker compromises a trusted website or online forum often visited by the target, possibly injecting malware to infect visiting users and gain access to their compromised machines. The term comes from the idea of targeting places where people naturally gather, like a physical waterhole.
Tailgating
A physical intrusion where the attacker bypasses security by following closely behind an authorised user into a secure area.
Reverse Social Engineering
The attacker gains credibility by assisting the victim with a problem, sometimes one the attacker secretly caused, before requesting sensitive information in return.
From Traditional Social Engineering to SEAR: AI-Augmented Attacks
For decades, social engineering relied on predictable tactics such as phishing emails, pretexting, and identity theft, exploiting trust through scripted interactions. While still effective, these methods lack the adaptability and personalisation seen in emerging threats. One such development is the Social Engineering Augmented Reality (SEAR) framework.
A recent Cornell University study shows that SEAR combines augmented reality’s real-time environmental awareness with the adaptive reasoning of large language models (LLMs) to deliver highly personalised attacks. In the experiment, attackers wearing AR glasses first engaged targets in a live, in-person conversation. The glasses captured facial expressions, vocal cues, and surrounding context, then merged this data with public social and professional information to build a detailed profile. Real-time prompts guided the attacker through a three-stage strategy: opening, engagement, and trust-building. Each response from the attacker was tailored to the victim’s responses.
The results were striking: following this initial face-to-face interaction, 93.3% of participants said they would click a photo link sent via email, 93% would accept social media friend requests, and 91% would engage via SMS. Success rates far above typical phishing campaigns.
SEAR marks a turning point in social engineering. By simulating genuine interpersonal familiarity, it breaks down the mental defences people rely on to spot deception. As this technology becomes more accessible, organisations must strengthen defences against attacks that can adapt in real time and exploit trust at scale.
Case Study: Scattered Spider (aka UNC3944)
In early 2025, Scattered Spider (tracked as UNC3944) continued to operate as one of the most sophisticated cyber threat groups targeting global enterprises. According to a joint CISA and FBI advisory, the group has engaged primarily in ransomware operations, leveraging social engineering, identity abuse, and cloud exploitation to gain access to target networks.
CISA and FBI reporting highlights UNC3944’s frequent use of impersonation, particularly posing as IT helpdesk staff via vishing or smishing to obtain credentials and convincing employees to share one-time passwords for MFA bypass.
Smarttech247’s own research expands on these findings, showing that their initial access methods also include phishing campaigns through fake support portals, insider recruitment for access credentials, and exploitation of exposed VPNs, Citrix environments, and misconfigured cloud services.
Once inside the network, the group conducting credential harvesting and scanning internally for high-value targets. Post-compromise, UNC3944 exfiltrate sensitive data, maintaining persistence through scheduled tasks and cloud services, deploying ransomware or selling access to other threat actors, and in some cases disrupting operations.
By combining living off the land techniques with targeted social engineering, UNC3944 can evade detection for extended periods, maximising the operational and financial impact on large enterprises.
UNC3944’s methods show that even well-defended organisations can be compromised through human and procedural weaknesses, not just technical flaws. Their focus on helpdesks, outsourced IT, and cloud misconfigurations highlights the need for layered defences, combining security awareness training, strict access controls, and proactive monitoring to detect unusual account activity before it escalates.
Case Study: The WinRAR Zero-Day Spear-Phishing Campaign
As reported by Help Net Security, a textbook spear-phishing campaign targeted companies in finance, manufacturing, defence, and logistics with convincing job-application emails. An example of social engineering, the messages appeared to come from legitimate candidates and included what seemed to be a harmless CV file.
In reality, the file contained malicious code designed to exploit a vulnerability in the popular file-compression tool WinRAR (CVE-2025-8088). When opened, it unpacked hidden malicious files capable of installing backdoors and configuring themselves to run automatically whenever the system restarted.
While the flaw itself was a technical vulnerability, the attackers’ entry point relied entirely on social engineering. They exploited the recipient’s trust in the hiring process to deliver the payload. No advanced intrusion techniques were required.
In this incident, none of the targeted organisations were ultimately compromised, but the attempt underscores the risk of blended threats, where human manipulation enables technical exploitation. It is precisely the type of scenario that social engineering penetration testing aims to detect and mitigate before an actual breach occurs.
Social Engineering Penetration Testing
Social engineering penetration testing identifies human vulnerabilities before a real attacker can exploit them. Even the most advanced firewalls, intrusion detection systems, and endpoint protections can be bypassed if an attacker convinces an employee to hand over credentials, open a malicious attachment, or grant physical access.
Effective social engineering pen tests simulate the tactics of real-world threat actors with the aim of manipulating, deceiving, and persuading employees into breaking security protocols. This can include phishing emails, vishing calls, smishing messages, or any other exploit covered earlier. The goal is to measure both staff awareness and the effectiveness of your policies, training, and incident response.
By mimicking an attacker’s methods without disrupting operations or compromising sensitive data, pen tests reveal how far an intruder could get using only persuasion and deception. They often uncover weaknesses missed by purely technical penetration testing.
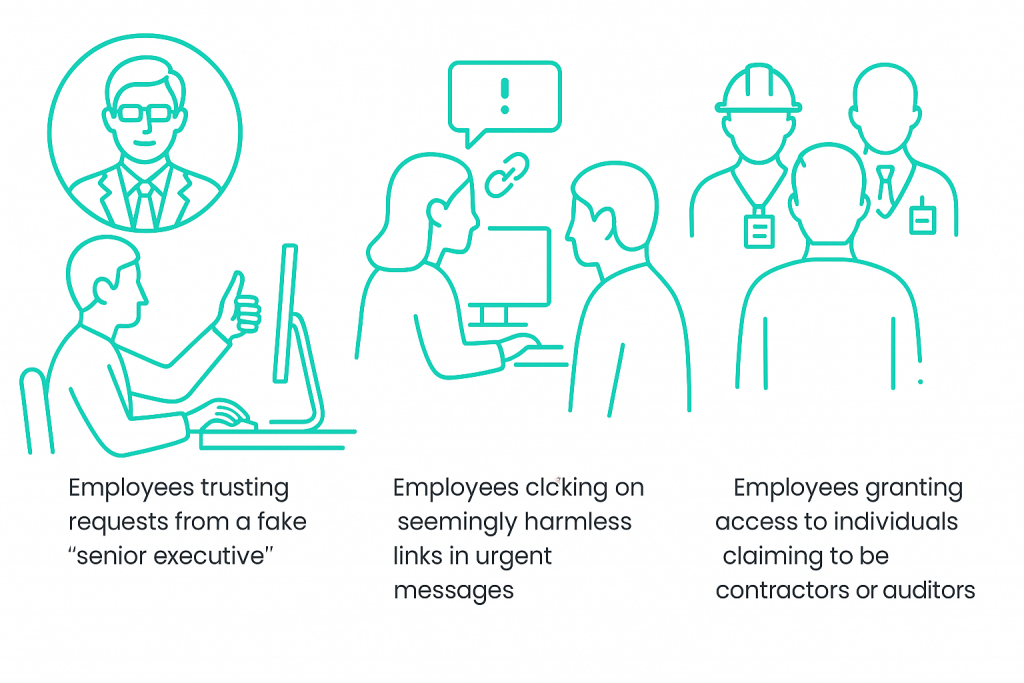
A typical engagement begins with reconnaissance to identify potential targets, followed by controlled attack scenarios to gauge susceptibility.
At the conclusion, a detailed report outlines which attempts succeeded, why they worked, and actionable steps to strengthen defences.
Social engineering penetration testing exposes the social and procedural gaps attackers exploit every day. Combined with technical penetration testing, it provides a complete, real-world view of your organisation’s attack surface.
Social Engineering Defences
The Principle of Least Privilege
When granting system access, users should receive only the minimum permissions necessary to complete their tasks. Organisation should separate access levels so no single individual can perform an entire chain of actions that could compromise the system. This limits the impact of insider threats and reduces the damage a successful social engineering attack could cause.
The Three As: Authentication, Authorisation, and Accounting
All employees should understand the three As, as they form a critical defence against social engineering. Attackers often attempt to bypass these controls by impersonating someone with legitimate access, persuading an employee to share login credentials, or requesting permissions they should not have.
- Authentication confirms a person’s identity before granting access, preventing attackers from relying solely on appearance or stolen credentials.
- Authorisation ensures that even if an attacker gains access, their actions are restricted, limiting potential damage.
- Accounting (or auditing) logs all activities, creating a traceable record that can help detect suspicious behaviour early and enable timely response.
When applied consistently, and when employees understand their role in maintaining them, these measures make social engineering attacks far less likely to succeed.
Awareness Training & Phishing Simulation
Security awareness training is one of the most effective defences against social engineering. Without regular assessment and realistic phishing simulations, staff may not recognise the subtle cues of a malicious email, a suspicious phone call, or conversations engineered to extract information. By training employees and assessing them through simulations, organisations can create a prepared workforce capable of identifying and stopping attacks before they cause damage.
Read More from Our Latest News:
- The UK’s cyber problem just got a price tag
 New UK research reveals the real cost of cyber attacks, from £195k per incident to £14.7bn annually. With four nationally significant attacks a week, the UK’s cyber threat is now a business and national resilience issue.
New UK research reveals the real cost of cyber attacks, from £195k per incident to £14.7bn annually. With four nationally significant attacks a week, the UK’s cyber threat is now a business and national resilience issue. - Smarttech247 Recognised for 2nd Year in Gartner’s Market Guide
 Smarttech247 (AIM: S247) recognised for the second year in Gartner’s Market Guide for Managed Detection and Response, reinforcing its AI-driven MDR expertise.
Smarttech247 (AIM: S247) recognised for the second year in Gartner’s Market Guide for Managed Detection and Response, reinforcing its AI-driven MDR expertise. - Smarttech247 Launches Fifth Edition of Women in Cybersecurity Academy
 Women in Cybersecurity Academy is a free six-week global learning initiative designed to empower women with the skills to pursue a career in cybersecurity.
Women in Cybersecurity Academy is a free six-week global learning initiative designed to empower women with the skills to pursue a career in cybersecurity.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.