Monday, August 25th, 2025
What Are Zero-Day Vulnerabilities and Why They Still Terrify


Zero-day vulnerabilities remain one of the most disruptive threats facing security teams. When a new exploit emerges, it often sparks chaos — attackers move quickly, and defenders scramble to identify exposure and apply mitigations.
Well-prepared organisations with mature vulnerability management programmes can respond more calmly. Their tools and processes allow them to identify affected systems quickly, isolate them, and apply patches or workarounds. For these companies, zero days have become less of a panic event and more of a controlled incident.
But for the majority, zero days are still a nightmare. Many organisations lack the basics: an accurate asset inventory, reliable patch management processes, and a culture of continuous vulnerability monitoring. As a result, they may not even know if they are exposed, or they discover the impact only after an attack.
The reality is that while technology and processes have improved, the uneven adoption of vulnerability management means zero-day exploits remain as dangerous as ever. In many cases, they are even more problematic, because attackers understand that most companies still don’t have the basics in place.
What is a Zero-Day Vulnerability & Why Many Organisations Still Struggle
A zero-day vulnerability is a security flaw unknown to both software vendors and developers. Because it hasn’t been identified, no patch or fix exists, leaving systems exposed. What makes zero-days especially dangerous is that attackers often discover and exploit them before defenders even know they exist, creating a critical window with no known protection.
While a small subset of mature organisations can respond quickly and calmly to zero-day threats, the majority are still far from that point. Many are not actively scanning, lack a defined process, or don’t have the resources to respond effectively. When zero-day exploits emerge, they are often ignorant of the exposure until an attacker takes advantage.
Log4j (Log4Shell) remains a prime example. Despite being well-known, organisations still struggle with how to detect Log4J. The reason isn’t a lack of awareness, it’s a lack of maturity. Too many organisations still rely on outdated practices, lack a complete asset inventory, or don’t have partners to support them. The result is that zero days don’t just cause panic in the moment; they continue to sit unaddressed in networks for years. Cisco ASA/FTD zero-days in the ArcaneDoor campaign underscored the same challenge: even large, well-resourced enterprises were exposed, proving how difficult zero-day response remains.
Mergers & Acquisitions: Avoiding the Risk of Inheriting a Breach
Mergers and acquisitions (M&A) bring their own cybersecurity risks. The last thing any company wants is to “acquire a data breach” along with a new business. Conducting security due diligence is therefore critical.
Pre-acquisition testing can reveal whether the target organisation is carrying hidden risks such as unpatched libraries, poor patching strategies, or immature security cultures. Post-acquisition assessments can help align the new entity with the parent organisation’s security standards and reduce inherited vulnerabilities.
The goal is twofold: uncover weaknesses before they become costly surprises, and educate acquired companies on the steps needed to raise their security maturity. Without this process, organisations risk introducing systemic vulnerabilities into their environment through acquisition.
The Role of Managed Services in Filling the Gaps
Even with strong tools in place, many organisations face the same challenge: limited staffing. Security teams are often stretched thin, and vulnerability management falls behind. This is why mdr solutions and trusted technology partners are playing a growing role.
By leaning on external expertise, organisations can ensure consistent vulnerability monitoring, prioritisation, and remediation — even if they lack the internal headcount. This has become one of the leading trends in vulnerability management: not just buying the tools, but securing the people and processes needed to make them effective.
Orchestration & Automation
One of the most effective ways to deal with the overwhelming number of vulnerabilities is through orchestration and automation. Modern platforms don’t just identify issues; they integrate with broader security ecosystems.
For example, APIs allow vulnerability data to flow directly into SIEM or SOAR platforms for unified reporting. Integrations with privileged access management solutions provide credentials for deeper scans, while ticketing systems like Jira or ServiceNow can be automatically populated with remediation tasks. This ensures accountability, creates a clear audit trail, and closes the loop between detection, prioritisation, and resolution.
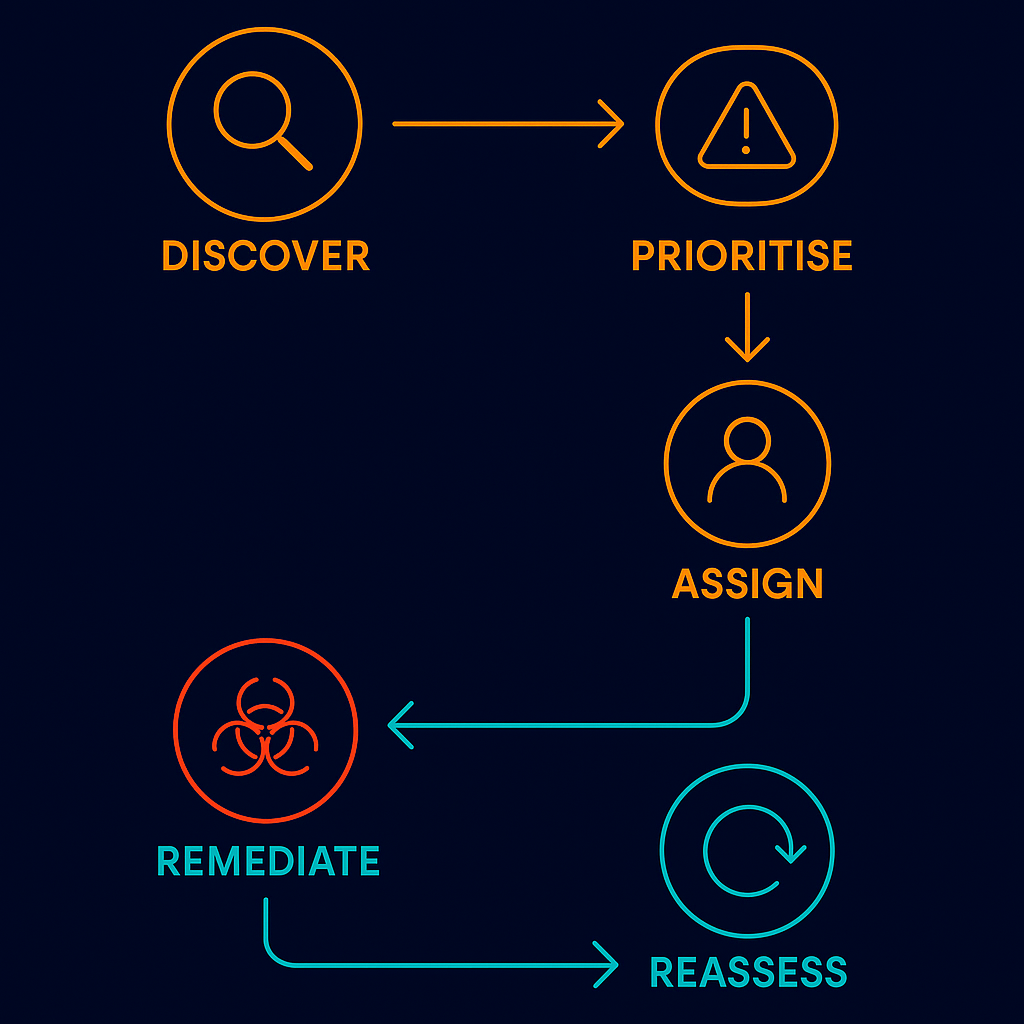
The key advantage here is not just technology, but accountability.
Once vulnerabilities are discovered and prioritised, they can be automatically assigned to the right teams, tracked through ticketing workflows, and resolved without the delays of manual handovers.
This creates a continuous cycle: discover → prioritise → assign → remediate → reassess.
Innovation Through Consolidated Vulnerability Management
One challenge for security providers is that every client environment is different. Enterprises often have a mix of vulnerability management tools and technologies, each with strengths and weaknesses. Managing this patchwork can lead to silos of information and inconsistent views of risk.
To address this, innovation is moving toward consolidated vulnerability management. By orchestrating multiple tools into a single view, organisations gain a unified perspective on their attack surface. Adding offensive security insights and engineering expertise to this mix makes the output more accurate and actionable.
The goal is not just to collect data, but to deliver a clear, prioritised view of vulnerabilities that reflects both technical severity and business impact.
Communicating Risk Without Alarmism
A unique challenge in vulnerability management is communicating findings to stakeholders. Delivering the results of an offensive security assessment can feel like “telling someone their baby is ugly.” No one likes to hear that their environment has major flaws.
The art lies in framing vulnerabilities as opportunities for improvement rather than criticisms. By explaining risks in terms of potential business impact — disruption of operations, financial losses, reputational damage — security teams can help stakeholders understand why addressing these issues matters. The goal is to build trust and partnership: the security team isn’t there to embarrass, but to strengthen the organisation’s maturity and resilience.
Compliance vs. Real Security
Another reality is that many organisations pursue vulnerability management primarily to achieve compliance badges such as ISO 27001 or PCI DSS. The risk is that compliance becomes a box-ticking exercise rather than a real improvement in security posture.
The better approach is to treat compliance as a by-product of strong security, not the end goal. Security assessments should go beyond what the auditor requires, exposing real-world threats and vulnerabilities. By aligning compliance efforts with genuine security improvements, organisations can both satisfy regulatory demands and build meaningful resilience.
The Role of AI in Vulnerability Management
Artificial intelligence is reshaping vulnerability management, acting as both a powerful defensive tool and a potential weapon for attackers. On the defensive side, AI can simplify complex tasks, making vulnerability management more accessible and efficient. Natural language queries allow security teams to ask questions like “What are my highest-risk vulnerabilities?” and receive immediate, actionable answers, reducing the time needed to identify priorities and eliminating hours of manual analysis.
However, the same technology introduces significant risks. Malicious actors are experimenting with training AI models to produce code laced with exploits, embedding malware into seemingly legitimate software, or using large language models to understand the typical technology footprints of industries such as energy, defence, or healthcare, making it easier to identify likely weaknesses. This dual nature of AI highlights both its promise and its danger: defenders must embrace the advantages it offers while implementing safeguards against its misuse.
Pros and Cons of AI in Vulnerability Management
| Pros (Defensive Use) | Cons (Offensive Risk) |
|---|---|
| Simplifies complex tasks in vulnerability management. | Large language models can map industry-specific technology footprints for weaknesses. |
| Natural language queries speed up risk identification. | Attackers can embed malware in AI-generated outputs. |
| Reduces time spent on manual dataset analysis. | Unsafeguarded AI adoption exposes organisations to new risks. |
The lesson is clear: AI adoption in cybersecurity must be approached with both optimism and caution. While it has enormous potential to streamline processes and strengthen defences, it will also create new opportunities for exploitation.
Tackling Zero-Days and the Next Era of Vulnerability Management
Looking out over the next 12–36 months, the industry faces a challenging future. The number of vulnerabilities detected daily continues to grow, accelerated by advances in generative AI and new technologies. This is pushing organisations to a breaking point: many will struggle to digest, prioritise, and assign resources fast enough to keep up.
The result will likely be more frequent breaches, with more severe consequences. To stay ahead, organisations must invest in maturing their practices — from asset discovery and attack surface management, to integrated vulnerability orchestration, to embedding AI responsibly into their workflows.
Zero-day vulnerabilities remain an especially difficult challenge, as no patches exist when they first emerge. In the absence of immediate fixes, organisations must minimise exposure through layered defences. That means applying patches quickly and consistently when they do become available, maintaining strong antivirus and firewall controls to block common attack vectors, restricting risky behaviours like the use of removable media, and cultivating a security-conscious culture where employees understand their role in protecting systems.
The direction of travel is clear: vulnerability management will only grow more complex, and only those organisations with strong processes, trusted partners, and a culture of continuous improvement will be positioned to keep pace.
Read More from Our Latest News:
- The UK’s cyber problem just got a price tag
 New UK research reveals the real cost of cyber attacks, from £195k per incident to £14.7bn annually. With four nationally significant attacks a week, the UK’s cyber threat is now a business and national resilience issue.
New UK research reveals the real cost of cyber attacks, from £195k per incident to £14.7bn annually. With four nationally significant attacks a week, the UK’s cyber threat is now a business and national resilience issue. - Smarttech247 Recognised for 2nd Year in Gartner’s Market Guide
 Smarttech247 (AIM: S247) recognised for the second year in Gartner’s Market Guide for Managed Detection and Response, reinforcing its AI-driven MDR expertise.
Smarttech247 (AIM: S247) recognised for the second year in Gartner’s Market Guide for Managed Detection and Response, reinforcing its AI-driven MDR expertise. - Smarttech247 Launches Fifth Edition of Women in Cybersecurity Academy
 Women in Cybersecurity Academy is a free six-week global learning initiative designed to empower women with the skills to pursue a career in cybersecurity.
Women in Cybersecurity Academy is a free six-week global learning initiative designed to empower women with the skills to pursue a career in cybersecurity.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.