Sunday, April 24th, 2016
IBM QRadar – Benefits of Managed SOC Services + Cases

At Smarttech we deliver managed SIEM (Security Information and Event Management) services to provide real-time analysis of your entire network system and a deeper visibility across your IT infrastructure through our Managed Security Operations Centre. The Smarttech security analysts manage and configure rules on the award winning IBM QRadar SIEM solution to fit the needs of our clients.
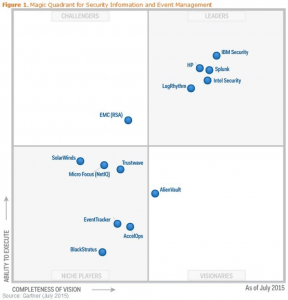 Moreover, IBM QRadar is in the SIEM leadership Magic Quadrant for the seventh consecutive year, highest on Ability to Execute (Y Axis) AND furthest to the right on Completeness of Vision (X Axis). Here are 5 advantages of managed SIEM services that our clients benefit from on a daily basis:
Moreover, IBM QRadar is in the SIEM leadership Magic Quadrant for the seventh consecutive year, highest on Ability to Execute (Y Axis) AND furthest to the right on Completeness of Vision (X Axis). Here are 5 advantages of managed SIEM services that our clients benefit from on a daily basis:
1. Immediate detection of suspicious log sources
Log collection is the heart and soul of a SIEM solution. The more log sources that are fed into the SIEM solution, the more can be accomplished with IBM QRadar. A common pattern we are finding among compromised log sources is that attackers tend to change the configuration files of endpoint agents installed and forward numerous irrelevant files to the Log Manager. This affects the performance of real-time searches that are configured and the storage capacity of the underlying index for storing logs. To counter such malformed actions, IBM QRadar can be configured to raise an alert whenever the amount of EPS (Events Per Second) from a log source exceeds a threshold value. It can also be configured to raise an alert if a host stops forwarding logs after a threshold limit.
2. Detecting access logs and Database Queries
In the age of ‘Big Data’ and large customer databases, companies are faced with a major risks and namely the access rights of high level employees to this data. With an Oracle database a user has the capabilities to turn off auditing of activity and cause havoc across the database.
IBM QRadar facilitates the reading of Level 7 network traffic information by sniffing the packets of data being sent through a remote session to the device where the database is stored. This allows us to find out the actions of the user deleting/modifying data while auditing is switched off and store this information within an offense, which is freely available to the persons monitoring the network security.
3. Customised rules for increased network security
Recently, one of our clients was looking for increased surveillance of user access within the main office building as well as an overall look at the access controls though external points, such as VPN. We devised a solution by utilising the IBM QRadar’s Log Management to allow us to not only gather the System logs from the Card Access Control system and the log files from the VPN connection, but to combine and collate them together within QRadar. This allowed us to create a rule that would fire an offense in the event that a user swipes a card into the office and also logs in via VPN connection. The offense can the trigger an email to be sent to any relevant person that would contain key information such as: username, Source/destination IP, device name as well as the events leading up to the offense.
The client was then faced with another business challenge, and namely how to fully detect and block insider confidential database information theft. We developed a solution whereby IBM QRadar would create an offense and trigger an alert, i.e. when customer databases would be sent though personal email (Gmail, Hotmail etc.) or when the users would have a web browser open accessing personal email websites. This type of alert would not be possible without IBM QRadar’s ability to gather system logs, as well as to read the information across the ingress and egress traffic to discover the web page that is open on any given computer on the monitored network.
4. Dealing with a compromised or infected system
In this day and age, obtaining 100% protection against threats is nearly impossible. However, products like IBM QRadar can provide early warnings and forensic capabilities for the clean-up process, should a company have the misfortune of being compromised. It collects logs from multiple sources including your Anti-Virus, Firewall, Web filters and IDS. Additionally, by using IBM’s X-FORCE Exchange Threat Intelligence Platform, QRadar can detect possible connections to Malware hosts and alert you before your system becomes compromised. This platform provides detailed information about vulnerabilities, IPs, URLs, and web applications. Its database includes information based on real-time monitoring of more than 15 billion security events every day, malware threat intelligence from a network of 270 million endpoints, threat information based on 25 billion web pages and images, details of 8 million spam and phishing attacks, and reputational data on close to a million malicious IP addresses.
5. Creating Reports on login failures on your network which are outside core business hours
Out of the box IBM QRadar comes with over a thousand reports ready to be activated. A report can consist of several data elements and can represent network and security data in a variety of styles, such as tables, line charts, pie charts, and bar charts. QRadar is able to automatically create a report based on the logs of users who failed to authenticate multiple times across a network within a certain time frame. This can be generated daily, weekly or monthly and is presented in a readable format via the SIEM Console or email.
If you would like to find out how IBM QRadar helps protect thousands of businesses everyday, contact our security experts for more information or simply chat to us here!
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.