Thursday, August 26th, 2021
Prometheus TDS: Campo Leader and Hanctor

Numerous cyber criminal groups are leveraging an underground service known as Prometheus TDS. This distributes a variety of malicious software distribution campaigns. They redirect visitors to phishing and malicious sites resulting in payload deployments such as Campo Loader and Hanctor.
Prometheus TDS
Prometheus is available for sale on underground platforms for $250 a month. The service is a Traffic Direction System (TDS) that is designed to distribute malware-laced Word and Excel documents, and divert users to phishing and malicious sites.
More than 3,000 email addresses have been targeted via malicious campaigns across multiple sectors in which Prometheus TDS was used. The underground MaaS solution has been used to distribute a wide range of malicious software distribution campaigns. They result in the deployment of payloads such as Campo Loader, Hancitor, QBot, Buer Loader, and SocGholish.
How Prometheus TDS works:
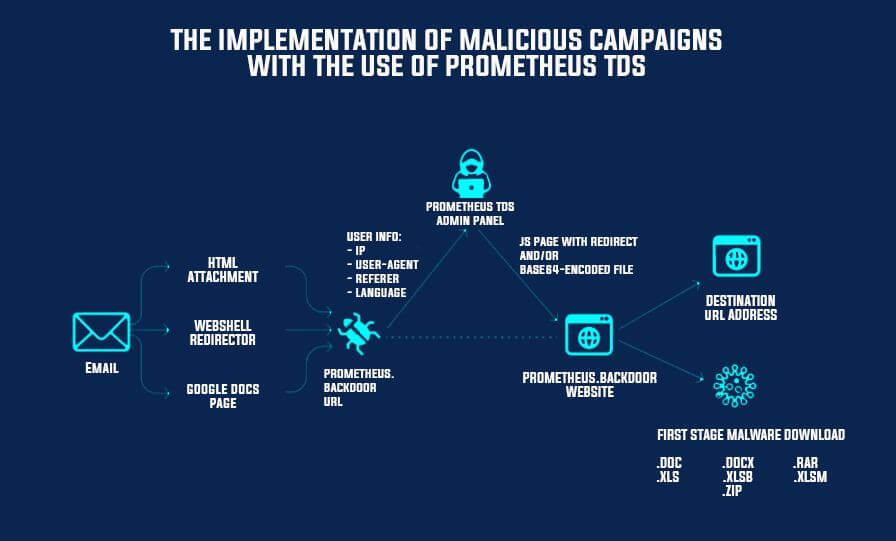
Malware gangs can access the Prometheus service for a fee where they receive an account on the TDS platform. The ‘renters of the service’ can then login to the account, configure the malware payload they want to distribute, the type of users they want to target and provide a list of hacked web servers.
Prometheus TDS scans the list of hacked websites provided by the hacker and deploy a backdoor to the hacked servers. The hackers can then move on to send email campaigns where the email text contains links to the hacked websites.
When the user clicks on a link or the HTML file attached – it will take them to the hacked site. This is where the “Prometheus.Backdoor” is uploaded to the compromised websites and collects the victims data. Analyzing the data, the panel decides to send the payload to the user or redirect them to the specified URL.
The service may send a malware-ridden Microsoft Word or Excel document, with the user redirected to a legitimate site like DocuSign immediately after downloading the file to mask the malicious activity.
Some of the targeted inboxes belonged to U.S. government agencies. Corporations in the banking and finance, retail, energy and mining, cybersecurity, healthcare, IT, and insurance sectors were also targeted.
Research
When investigating the Prometheus TDS malware campaigns, the researchers at GroupIB found a lot of malicious Office documents that delivered Campo Loader, Hancitor, QBot, IcedID, Buer Loader, and SocGholish. These trojans are of course malware downloaders which were involved in the earlier stages of ransomware attacks over the last few years – Ryuk, Egregor, RansomExx, REvil, and Conti.
We are seeing in many malware campaigns today that there are always at least two if not three different groups working together to provide various services and Prometheus TDS has been no different.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.