Friday, January 14th, 2022
Applications Exploited for Spear Phishing

Introduction
Social engineering such as spear phishing is a technique used by cybercriminals to trick people into revealing valuable information such as passwords. This technique is generally used as part of the initial stages of a cyberattack. Phishing is an umbrella term for social engineering attacks that are carried out via emails. Bad threat actors send out several maliciously crafted emails in bulk, like a “spray and pray” approach.
Spear Phishing
Spear phishing is an email-based attack that is intentionally aimed at a specific person. For example, whaling is a spear-phishing attack that targets senior management or company executives such as CFOs. If these attacks are successful, it can have disastrous consequences for organisations such as malware injection, ransomware or data breaches. These can result in organisations incurring huge financial costs to restore access to their systems and information. Not only that, organisations can face huge fines of up to €20 million should they experience a data breach.
Google Docs
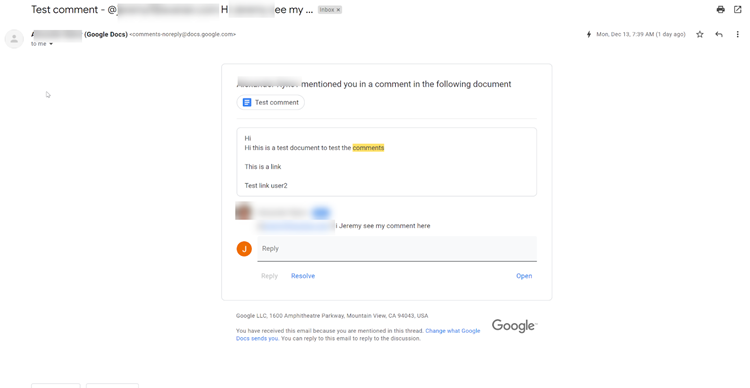
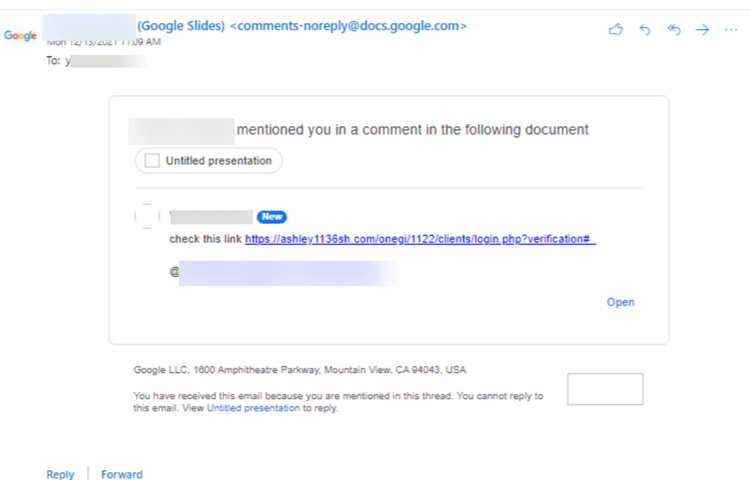
A recent campaign of spear phishing that exploits Google’s cloud-based Google Docs, which began to emerge in October 2021, has exploded earlier this month. Attackers have exploited the comments feature on it in order to send malicious links to the thousands of email inboxes. As the email is being sent from a legitimate Google email address, it can bypass the email security within Google or Outlook. The attackers would tag/mention (‘@’) the particular person’s email address within the comment. A mention notification email would then be sent to that person’s inbox.
A malicious link is hidden within the comment in the notification email received. This link can lead to a malware landing page or phishing site. These pages are crafted to mimic trusted services such as Google in order to trick the user into inputting their credentials. These compromised credentials can then be used by the attacker to further infiltrate the organisation’s network. Additionally, the attacker’s email address cannot be seen in the email, the email recipient can only see a name. This makes it much easier for the attacker to impersonate someone within the victim’s social or professional network. For example, an attacker can simply carry out a search on social media sites or the company website to obtain a name that the victim would be familiar with. It has also been reported that this method can also be leveraged on Google Slide.
Below are examples of these notification emails for Google Docs and Google Slides, as tested by Avanan researchers (Source: Avanan).
How can users mitigate against similar spear-phishing campaigns?
Hover over the commenter’s name to verify their email address and full name, before clicking on the Google Docs comment link. Always check for the typical signs of a phishing email, such as:
- – Unexpected and non-topical emails
- – Emphasising an urgency for the user to act on the email
- – Containing suspicious links once the user hovers the mouse over the embedded link
- – Spelling mistakes or poor grammar
- If in doubt, always report any suspicious emails to your manager or reach out to the sender separately to confirm that the email was truly sent by them
How can organisations strengthen their ‘human firewall’ to protect themselves from similar campaigns?
- Organisations can implement anti-phishing tools. For example, Smarttech247’s NoPhish platform which detects and responds to suspected phishing attacks in real time. As a user-friendly tool, it sits on the Microsoft Outlook ribbon for the user to click on whenever they receive a suspicious email.
- Ensure that phishing is part of the organisation’s regular information security awareness training. To supplement this, phishing simulations should be carried out on a regular basis. These simulations can help identify further training needs and help maintain a good level of email security awareness.
- As part of an Incident Response Plan, there should be a clear process for how employees should manage suspicious emails. This process should be easy to follow. For instance, this process can be communicated to all employees through a checklist format.
This new wave of spear-phishing attacks reminds us that legitimate applications will continue to be weaponised. As is the case for many social engineering attacks, cybercriminals will continue to exploit the element of trust. As services such as the Google Workspace suite are generally used on a daily basis, many users are familiar with the Google brand. This familiarity can create a level of trust that may bring down the user’s security awareness. Perhaps the key defence to preventing these attacks is to follow the main principle in Zero Trust – to always verify explicitly.
Author: Mae Patlong, Information Security Consultant, Smarttech247
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.