Monday, August 10th, 2015
Introduction To Penetration Testing

Every day we hear about successful high profile attacks that have been able to exploit vulnerability on a corporate network and extract valuable data. Whether this is in the form of credit card details, medical records or other personal information the question posed by IT managers remains the same. How can we ensure our perimeter/network is secure? The answer is a penetration test!
Pen testing is without a doubt one of the most important security activities an IT department can conduct. After all, a company can spend huge sums of money on expensive security solution to protect each vector. Only to find that they have been infiltrated by an external hacker or piece of malware with relative ease. At the end of the day it could simply be human error (it usually is) and it is something which cannot be accounted for without an evaluation.
We had a client recently who purchased a very expensive enterprise level security system who, through a pen test, realised that a simple configuration issue had led to a massive vulnerability! This can be avoided by being diligent and scheduling regular pen test at least once a year. Given the time, money and resources that go into purchasing security software & hardware in the first place you would be surprised how often this is overlooked.
It’s understandable that IT departments are extremely busy, however, MAKE TIME as it could save your company and your job!
Pen Testing – Holistic View
Pen testing can be largely misunderstood. This is due to a lack of purpose, direction and of course because of marketing’s many different names. You may have heard the terms network audit, security assessment, vulnerability scan etc. What they are promoting are assessment tools that fit into a more ideological state of perfect IT security protocols. In reality companies do not have the budget or reources for this, so a pen test is in order.
The point to remember is that a pen test is conclusive. It actually penetrates your network in real life, so you have an accurate picture of the state of your IT security posture. No theoretical pieces about how your company should be safe because of xyz, it’s the practical facts of how safe you ACTUALLY are!
Below you will find an infographic representing a holistic view of Network testing:
[cols][col-large]
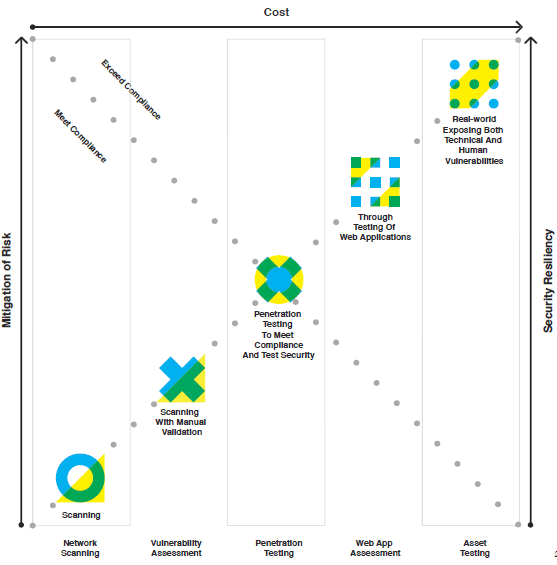
[/col-large][col-small]
To conclude, people make mistakes in life and IT personal are no different.
The problem with IT staff making mistakes; is that there can be catastrophic results. It can affect for your company’s finances, reputation and for any customers should you lose their data.
Your network needs to be checked for real life vulnerabilities. This will allow you to gain an accurate picture of where you stand and what you need to fix.
At Smarttech we conduct basic penetration testing and full penetration testing for our customers.
[/col-small][/cols]
Basic Penetration Testing
Smarttech Basic Penetration Testing services help organisations remain compliant. This is done by making sure that their network’s configuration and patch management are up-to-date. We take proactive and fully authorised attempts to improve your security by simulating an exploit and exploring potential vulnerable areas.
Full Penetration Testing
Smarttech Full Penetration Testing services fully evaluate an organisation’s network, applications, endpoints and internal/external attempts to infiltrate its security points. We will dive deeper into your network’s infrastructure to provide a full overview of vulnerable and compromised areas that hackers could exploit.
If you have any questions OR you would like a free consultation please don’t hesitate to get in touch with us.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.