Friday, January 28th, 2022
Nation-State Cyber Attacks Impact

Nation-state cyberattacks are on the rise. As part of Smarttech247’s Cybersecurity Insights Report, a trend of nation-state attacks has been ranked in our top 10 predictions for 2022. These attacks are not only for governments and should be considered by CISOs in the coming year. In 2021 alone, we saw the United States experience nation-state supply chain cyberattacks, such as the SolarWinds breach. Although any nation irrespective of size and wealth can execute a cyberattack against any other nation or organisation, it is generally countries in Europe and North America that are more vulnerable to these attacks. As highlighted in the Smarttech247 report, this is due to their heavier reliance on information systems and having more critical infrastructure connectivity compared to less-developed nations.
What defines nation-states as threat actors?
They generally have much more resources at their disposal and access to more information compared to a lone hacker or other hacker groups. As a result, these actors have a higher level of sophistication and have the ability to carry out advanced persistent threats (APTs). This is why you may often hear the term “APT Groups”. APTs are cyberattacks that are carried out as stealthily as possible in order to remain undetected and stay in the network for as long as possible (months and even years). These attacks generally have the objective of harvesting valuable information. For instance, APTs use lateral movement (moving laterally across the target’s network) and remain undetected by blending in with the target organisation’s usual network traffic.
Defense Report
The recent Microsoft Digital Defense Report highlighted that 2021 saw Russia position itself as the “most active attacker”, which was previously held by North Korea. While the targets, tools and attack methods may vary, nation-state attackers are typically not motivated by the potential financial gains. They often have the goal of intelligence gathering for geopolitical reasons or stealing an organisation’s intellectual property within their nation’s interest. MITRE identify and maintain a list of profiles for these APT groups or nation-states actors, such as the techniques and software used by each group.
Ukraine
One of the most recent cyberattacks carried out by a suspected nation-state actor was experienced by the Ukrainian government earlier this month. This resulted in approximately 70 government websites becoming unavailable. It was reported that even the National Emergency Service websites and state websites that stored electronic passports and vaccination certificates were also impacted by the attack. Due to the current political climate, it is suspected that the threat actor responsible is linked to Russia. The Microsoft Threat Intelligence Center has published that this attack was a result of destructive/data-wiping malware. It was designed to appear as ransomware, but the malicious software did not have a ransom recovery mechanism. This destructive code was designed to render targeted devices inoperable and be destructive, rather than to retrieve a ransom.
Microsoft also found that this malware is being used to target organisations in Ukraine, not just governmental bodies. Nation-state actors do not only target governments. Any organisation that this attacker deems to hold potentially highly valuable information can become a target.
CISO’s should still keep this type of attack in mind when considering possible threats and assessing the effectiveness of the security controls in place. As the attack techniques used by this threat actor are similar to that of an attacker, organisations should consider the following:
Mitigation
- Ensure that security controls (technical & organisational) remain effective against the current threat landscape.
- All cyberattacks, regardless of the type of threat actor, have an attack lifecycle and need an initial point of entry into the target organisation’s network. Organisations should ensure that there all possible attack vectors have efficient security controls in place, such as:
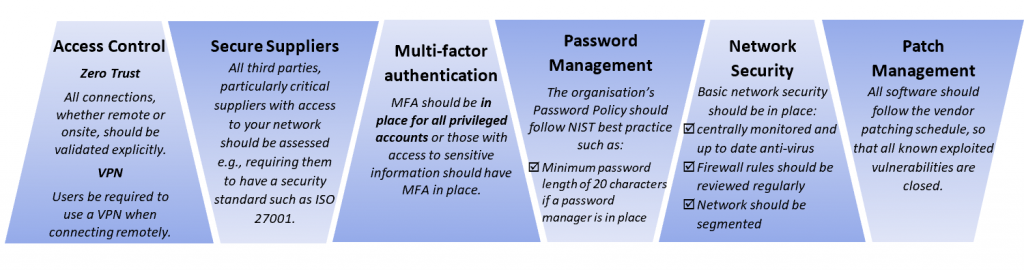
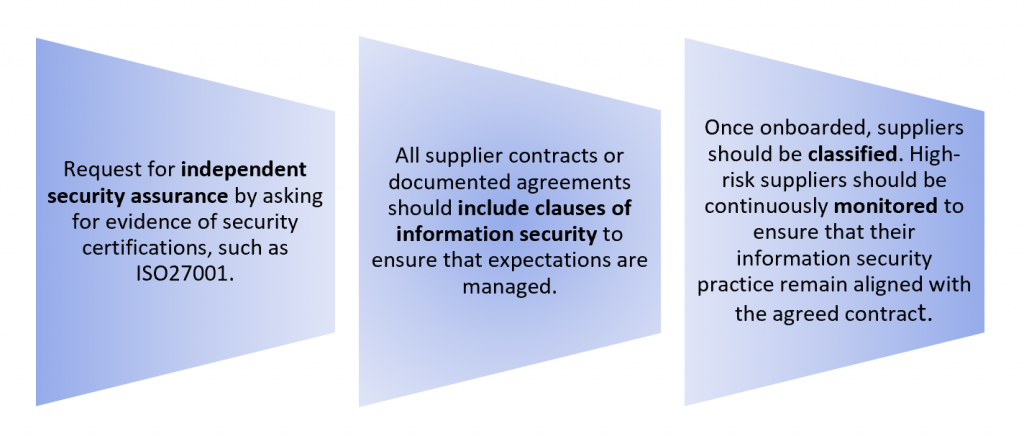
- Monitor high-risk third parties with access to your systems and network. For example, due to the current political situation and cyberattacks in Ukraine, it is important to carefully monitor any incoming traffic from Ukrainian organisations due to the higher probability of a potential supply chain attack. It is important for organisations to gain full visibility and understanding of the risks associated with their supply chain. As such all potential suppliers/third-parties should be properly assessed prior to onboarding.
When assessing which security controls to implement and how it is important to remember there is no silver bullet solution that will provide 100% security 100% of the time. It is a matter of which controls can create the biggest hurdles for attackers to get to the organisation’s critical assets. The security solutions in place should lengthen the amount of time that hackers need to infiltrate the network. At the same time, organisations should ensure a fast incident detection rate to be able to stop cyberattacks at their early stages and minimise their impact. For example, a zero-trust network creates more challenges for hackers to overcome and more opportunities for organisations to detect the attacker due to its principle to always verify explicitly.
Author: Mae Patlong, Information Security Consultant, Smarttech247
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.