Wednesday, July 30th, 2025
How Attack Surface Management Works


Every attack starts with an objective: compromising something valuable. In cybersecurity, those valuable targets are your assets, anything your organisation relies on to operate, compete, or comply. These assets might be physical (hardware, infrastructure), digital (applications, data), or intangible (intellectual property, brand reputation). Effective attack surface management (ASM) begins with understanding what these assets are, where they reside, and how they might be exposed.
How Attacks Target the Surface
An attack is any deliberate action aimed at compromising, stealing, damaging, or interfering with those assets. Some attacks aim to observe silently (passive), others to disrupt or alter (active). Whether targeted or indiscriminate, every attack requires a way in, and ASM exists to detect, map, and monitor those paths.
Attack Vectors and ASM’s Monitoring Role
The attack vector is the route used to breach your environment. Successful ASM will continuously monitor these vectors to identify new risks and eliminate blind spots. The attack vector is the method in which the attacker gains access to the system.
The most common vectors include:
- Phishing
- Ransomware
- Third-party vendors
- Compromised credentials
- Misconfiguration
- Unpatched vulnerabilities
- Poor encryption
- Insider threats
Mapping and Managing the Attack Surface
An organisation’s attack surface is the collection of all potential vulnerabilities and exposure points, whether known, unknown, visible, or hidden. It’s where attacks begin. ASM is the continuous effort to discover, map, and monitor this surface. It enables organisations to stay ahead of evolving threats by understanding where they are most exposed and how those exposures change over time.
A comprehensive ASM process looks beyond just known systems. It accounts for cloud services, shadow IT, forgotten subdomains, open ports, misconfigurations, and even vulnerable public-facing APIs. Larger attack surfaces typically signal greater risk, making visibility and reduction critical priorities.
Categories of Attack Surfaces ASM Must Address
ASM categorises the attack surface into three main domains:
Digital attack surfaces: Exposures related to software, systems, networks, and internet-facing services.
Physical attack surfaces: Points of physical access that allow direct compromise of systems or infrastructure.
Social engineering: Human-centric vulnerabilities that allow manipulation and credential theft.
ASM’s job is to help security teams monitor all three, identify weak spots, and drive mitigation.
Advanced Persistent Threats and ASM’s Detection Role
A particularly critical threat IT directors and CISOs need to consider is the Advanced Persistent Threat (APT). An APT is a sustained and targeted attack in which adversaries gain unauthorized access to a system and remain undetected for an extended period. These attacks often exploit multiple vulnerabilities across different systems and can persist for months. The nature of APTs makes them difficult to detect using traditional security tools.
ASM plays a key role in identifying the subtle indicators of these long-term intrusions. By maintaining continuous visibility across the digital environment and mapping all access points, ASM helps uncover previously unknown vulnerabilities that an APT might exploit. It also supports threat hunting by giving analysts a complete view of the organisation’s exposure.
Entry Points ASM Needs to Control
Potential entry points for attackers include:
- Hardware
- Software
- People
- Process
- Network
- Data
Successful Attack surface management needs to take account of all these possible entry points.
Risk: The Core Driver Behind ASM
Managing risk is the driving purpose behind attack surface management. ASM exists to uncover, quantify, and reduce the areas of exposure that leave systems vulnerable. According to ISO (3100:2018), risk is defined as the effect of uncertainty on objectives. When aligned to ASM, that means the uncertainty introduced by unmonitored assets, misconfigurations, outdated systems, or unknown vulnerabilities.
To properly evaluate risk within ASM, organisations must classify exposures into clear categories:
- Acceptable: These risks present minimal impact and can be tolerated as part of standard operations.
- Tolerable: These risks require monitoring and limited mitigation but do not breach organisational thresholds.
- Intolerable: These require immediate response, either through patching, isolation, or replacement of vulnerable assets.
ASM platforms help security teams identify, score, and prioritize these risks in real time so that the most dangerous exposures are dealt with first.
Digital Threat Tactics That Expand the Surface
Attackers use specific techniques to exploit digital vulnerabilities. These tactics target communication paths, data states, and authentication flows. ASM’s role is to detect exposure to such methods before exploitation occurs:
- Interception: Unauthorized access to data in transit, such as network sniffing.
- Modification: Changing intercepted data before it reaches its target.
- Interruption: Disruption of services or communications, like denial-of-service attacks.
- Replay: Capturing and resending data to impersonate valid transactions.
- Fabrication: Injecting false data or commands into a trusted system.
By identifying systems susceptible to these techniques, ASM reduces surface-level risk before attackers can capitalize on it.
Human Factors as a Surface Expansion Risk
Technology isn’t the only contributor to a growing attack surface. Some of the most significant risks stem from people within the organisation. The human factor in attack surface management refers to behaviours, decision-making, and actions that can unintentionally introduce vulnerabilities. Environments that overlook the human element are more prone to risky behaviour, including the use of unauthorised tools (shadow IT) and poor adherence to cybersecurity practices.
ASM must incorporate human activity into its monitoring scope. This includes identifying patterns of access, misuse, and unsafe behaviour that could lead to unintentional exposure or exploitation.
Social Engineering and ASM Exposure
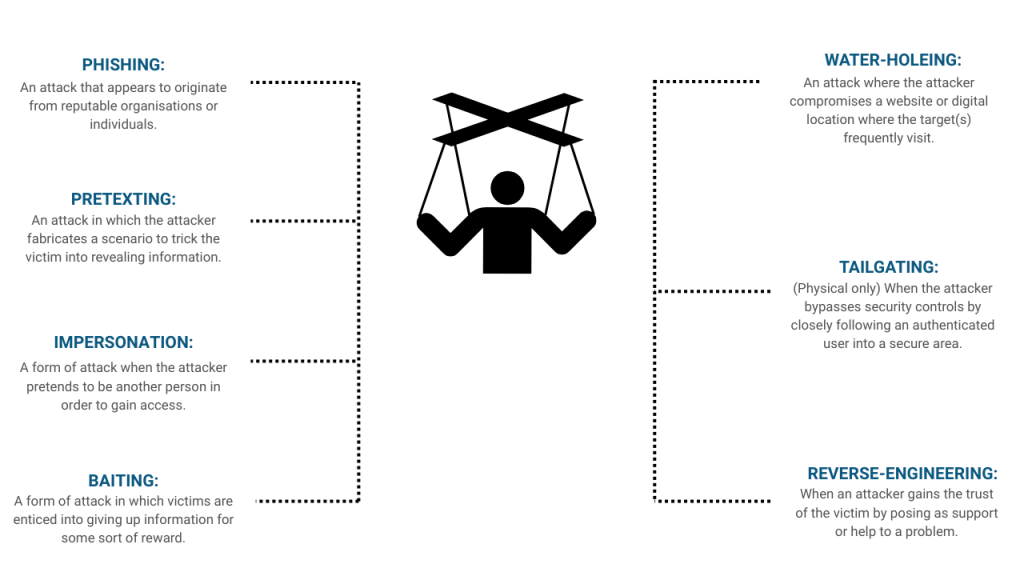
Social engineering is a method of attack that targets human psychology rather than technical vulnerabilities. It involves manipulating individuals into revealing sensitive information or granting unauthorised access. These attacks can be highly effective because they bypass many traditional security controls.
ASM must factor in the possibility of these exploits by monitoring access patterns, unusual activity, and behaviours that signal deception or coercion. Some of the most common social engineering tactics include:
- Phishing: Disguising malicious messages as communication from trusted entities.
- Pretexting: Creating a false scenario to extract information or access.
- Impersonation: Pretending to be someone with legitimate access rights.
- Baiting: Offering something enticing to lure victims into sharing sensitive data.
- Water-holing: Compromising websites frequently visited by a targeted group.
- Tailgating: Gaining physical access by following an authorised individual.
- Reverse engineering: Gaining trust by posing as technical support or help personnel.
ASM strategies must be designed to flag signs of manipulation and misuse stemming from social engineering tactics.
Comprehensive System Security as an ASM Outcome
Attack surface management is only as effective as the security posture of the systems it monitors. IT directors and CISOs must understand that complete control over the attack surface depends on securing every layer, applications, infrastructure, users, and operational processes.
ASM and Patch Management
Patch management is one of the most direct methods ASM can use to reduce risk. ASM identifies outdated or unpatched systems, triggering prioritised updates that reduce known vulnerabilities, especially zero-day threats. ASM doesn’t replace patching, it directs it.
Obsolete Systems and ASM Containment
Legacy or unsupported systems often cannot be updated but still serve critical business functions. ASM helps contain these systems by:
- Limiting network exposure
- Disabling all non-essential services
- Isolating them from broader environments
- Monitoring them more aggressively for compromise
If compromise is suspected, systems should be wiped, rebuilt, and tightly controlled moving forward.
Operational Controls Supported by ASM
ASM supports traditional technical controls such as:
- Antivirus and firewalls to block obvious threats
- MFA and access control to restrict lateral movement
- Logging and monitoring to provide incident insight
- Staff training and policy enforcement to reduce human error
ASM strengthens these by continuously validating where they are missing or ineffective.
ISO 27001 and ASM Alignment
ISO 27001 sets out a systematic approach to information security management. ASM directly supports ISO objectives by providing visibility of the current attack surface, quantifying associated risks, and monitoring mitigation efforts over time. Organisations using ASM are better positioned to demonstrate compliance, reduce risk, and meet regulatory requirements like GDPR.

Conclusion
Attack surface management is not just a technology layer; it’s a strategic discipline. It links risk, visibility, and action into a continuous cycle that helps organisations defend what matters most. From human error to legacy tech to sophisticated external threats, ASM gives CISOs and IT leaders the insight they need to act early and decisively. It’s not just about knowing what’s exposed. It’s about knowing what to do about it.
Read More from Our Latest News:
- The UK’s cyber problem just got a price tag
 New UK research reveals the real cost of cyber attacks, from £195k per incident to £14.7bn annually. With four nationally significant attacks a week, the UK’s cyber threat is now a business and national resilience issue.
New UK research reveals the real cost of cyber attacks, from £195k per incident to £14.7bn annually. With four nationally significant attacks a week, the UK’s cyber threat is now a business and national resilience issue. - Smarttech247 Recognised for 2nd Year in Gartner’s Market Guide
 Smarttech247 (AIM: S247) recognised for the second year in Gartner’s Market Guide for Managed Detection and Response, reinforcing its AI-driven MDR expertise.
Smarttech247 (AIM: S247) recognised for the second year in Gartner’s Market Guide for Managed Detection and Response, reinforcing its AI-driven MDR expertise. - Smarttech247 Launches Fifth Edition of Women in Cybersecurity Academy
 Women in Cybersecurity Academy is a free six-week global learning initiative designed to empower women with the skills to pursue a career in cybersecurity.
Women in Cybersecurity Academy is a free six-week global learning initiative designed to empower women with the skills to pursue a career in cybersecurity.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.