Thursday, September 1st, 2016
Don’t trust any USB devices. Ever

Most of you have probably heard of attacks through USB devices, but do you know where exactly the risks lie?
In today’s Tech Thursday we will show you the so called BadUSB attack and the risk of trusting USB devices.
You might say “I’m not scared, I have an Anti Virus and IDS system”
Some of you may think that the problem with the USB pendrive security refers to files being infected with a virus. So, the most sophisticated up to date Anti Virus software will protect you from the blast, right? … Wrong! The problem lies with the USB device itself. It’s not actually delivering any virus – it just acts differently than you may think.
What is this attack then?
It all began in 2014 when security researchers presented at the BlackHat conference a problem with USB devices. The problem relies on the fact that USB (as the name suggests: Universal Serial Bus) can support any type of device: storage, microphones, keyboards, cameras etc. The information about what type of device it is, is actually being communicated by the device itself and the operating system will simply trust that information.
Every USB device has a microcomputer that is responsible for the communication and as every computer device, it can be programmed to work in a completely different way that what it was designed for.
So what you might think is a USB camera, lamp, fan or mouse, it can actually be something completely different:
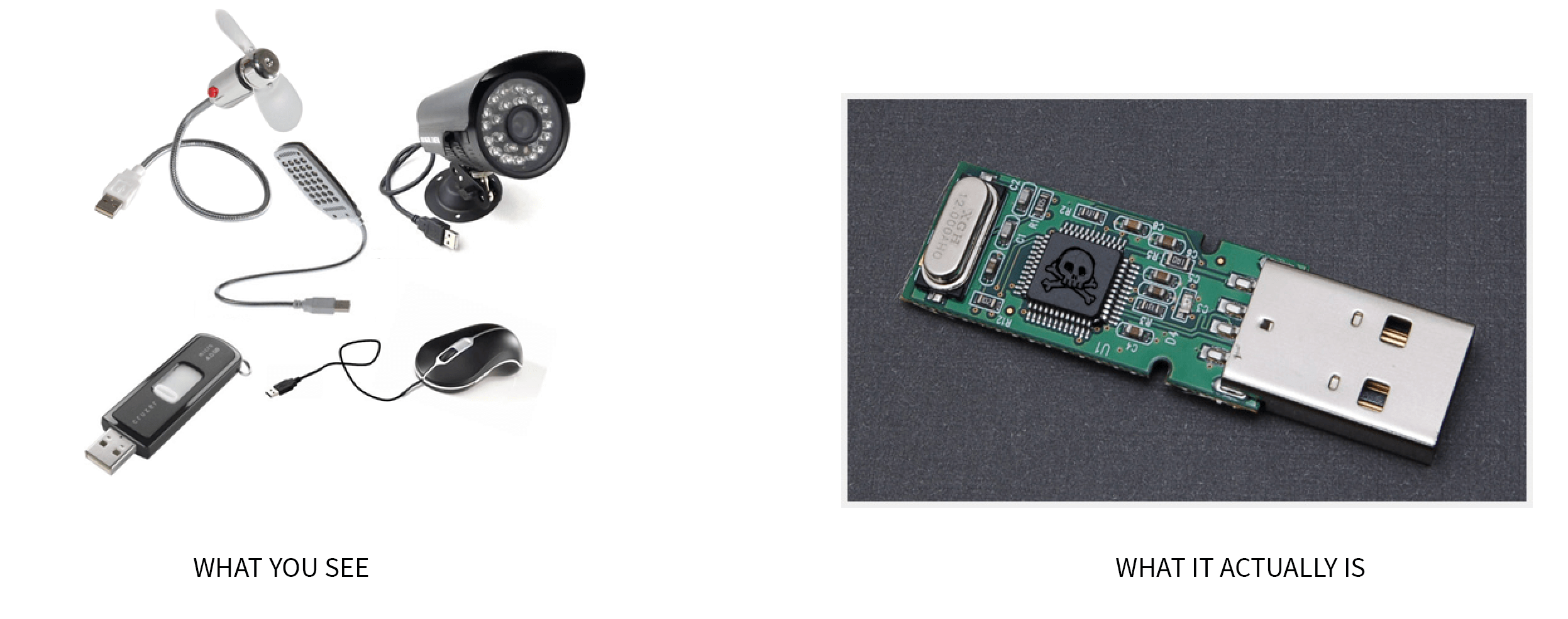
Hello, I’m a USB. What would YOU like me to be?
Now imagine that a simple USB pendrive can present itself to the computer as a keyboard. It can be programmed to enter any combination of keys and so any commands that will be executed as if they were entered directly from the computer’s keyboard.
Of course this kind of attack requires a direct access to the victim’s computer. This is where social engineering comes in.
On the latest security conferences it was confirmed by many researchers that the so called “drop by” USB attacks have an approximate 45% success rate – as we know, the human is always the weakest link in the IT security.
Countermeasures – what can You do?
There is no proper line of defence. The USB itself doesn’t deliver any solution to verify the connected device and there are no access control rules to manage the permissions for those devices (like it works for mobile applications – which in fact could be a good way for future mitigation techniques of this problem).
No Antivirus software will discover the attacks, as mentioned above, it is not a virus that gets through.
Also, certain IDS and SIEM solutions are advertised as a way to mitigate the risks but those can only detect the ongoing attack. Due to the fact that this attack takes seconds to deploy, there may be no time to react.
The only “working” solution is not to trust any USB devices either by having a “No USB” policy or using a sandboxed (offline) computer to test any USB device before it’s plugged into target computer. Companies that implement Information Security standards, like ISO27001, have great cryptographic controls that protect organisations from exactly these types of attacks, once implemented. If you want to learn more about the best security controls for your organisation, do not hesitate to contact us at any time.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.