Friday, December 16th, 2022
Cybersecurity Week in Review (16/12/22)

Hackers target Japanese politicians with new MirrorStealer malware
A campaign targeting Japanese politicians for weeks before the House of Councilors election in July 2022 has been attributed to a hacking operation known as Mirrorface. The group used a previously undocumented credentials stealer named MirrorStealer and deployed the new information-stealing malware along with the group’s signature backdoor, LODEINFO, which communicated with a C2 server known to belong to APT10 infrastructure.
The MirrorFace hacking group (APT10 and Cicada) began sending spear-phishing emails to their targets on June 29, 2022, pretending to be PR agents from the recipient’s political party, asking them to post video files on social media. In other cases, the threat actors impersonated a Japanese ministry, attaching decoy documents that extract WinRAR archives in the background. The archive contained an encrypted copy of the LODEINFO malware, a malicious DLL loader, and an innocuous application (K7Security Suite) used for DLL search order hijacking.
APT10 used LODEINFO to deploy MirrorStealer (‘31558_n.dll’) on compromised systems. MirrorStealer targets credentials stored in web browsers and email clients, including ‘Becky!,’ an email client popular in Japan. All stolen credentials are stored in a txt file in the TEMP directory and then wait for LODEINFO to send them to the C2, as MirrorStealer does not support data exfiltration on its own. LODEINFO is also used as a connecting bridge between the C2 and MirrorStealer, to convey commands to the info-stealer.
APT10 wasn’t very careful in this campaign, failing to remove all traces of its activity on the breached computers and leaving MirrorStealer’s text file containing the collected credentials behind.
Hacking Using SVG Files to Smuggle QBot Malware onto Windows Systems
Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG) images embedded in HTML email attachments. HTML smuggling is a technique that relies on using legitimate features of HTML and JavaScript to run encoded malicious code contained within the lure attachment and assemble the payload on a victim’s machine as opposed to making an HTTP request to fetch the malware from a remote server.
The idea is to evade email gateways by storing a binary in the form of a JavaScript code that’s decoded and downloaded when opened via a web browser. The attack chain concerns a JavaScript that’s smuggled inside of the SVG image and executed when the unsuspecting email recipient launches the HTML attachment.
When the victim opens the HTML attachment from the email, the smuggled JavaScript code inside the SVG activates, creating a malicious ZIP archive and then presenting the user with a dialog box to save the file. The ZIP archive is also password-protected, requiring users to enter a password displayed in the HTML attachment, after which an ISO image is extracted to run the Qakbot trojan.
HTML smuggling’s ability to bypass content scanning filters means that this technique will probably be adopted by more threat actors and used with increasing frequency.
Source – https://thehackernews.com/2022/12/hacking-using-svg-files-to-smuggle-qbot.html
New Actively Exploited Zero-Day Vulnerability Discovered in Apple Products
Apple on Tuesday rolled out security updates to iOS, iPadOS, macOS, tvOS, and Safari web browser to address a new zero-day vulnerability that could result in the execution of malicious code. Tracked as CVE-2022-42856, the tech giant has described the issue as a type confusion issue in the WebKit browser engine that could be triggered when processing specially crafted content, leading to arbitrary code execution.
While details surrounding the exact nature of the attacks have yet to be revealed, it’s believed that it was a result of social engineering or a watering hole to infect the devices when visiting a rogue or legitimate-but-compromised domain via the browser. Every third-party web browser that’s available for iOS and iPadOS, including Google Chrome, Mozilla Firefox, and Microsoft Edge, and others, is required to use the WebKit rendering engine due to restrictions imposed by Apple.
The update, which is available with iOS 15.7.2, iPadOS 15.7.2, macOS Ventura 13.1, tvOS 16.2, and Safari 16.2, arrives two weeks after Apple patched the same bug in iOS 16.1.2 on November 30, 2022.
The fix marks the resolution of the tenth zero-day vulnerability discovered in Apple software since the start of the year. It’s also the ninth actively exploited zero-day flaw in 2022 –
• CVE-2022-22587 (IOMobileFrameBuffer) – A malicious application may be able to execute arbitrary code with kernel privileges
• CVE-2022-22594 (WebKit Storage) – A website may be able to track sensitive user information (publicly known but not actively exploited)
• CVE-2022-22620 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
• CVE-2022-22674 (Intel Graphics Driver) – An application may be able to read kernel memory
• CVE-2022-22675 (AppleAVD) – An application may be able to execute arbitrary code with kernel privileges
• CVE-2022-32893 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution
• CVE-2022-32894 (Kernel) – An application may be able to execute arbitrary code with kernel privileges
• CVE-2022-32917 (Kernel) – An application may be able to execute arbitrary code with kernel privileges
• CVE-2022-42827 (Kernel) – An application may be able to execute arbitrary code with kernel privileges
The latest iOS, iPadOS, and macOS updates also introduce a new security feature called Advanced Data Protection for iCloud that expands end-to-end encryption (E2EE) to iCloud Backup, Notes, Photos, and more.
Source – https://thehackernews.com/2022/12/new-actively-exploited-zero-day.html
New GoTrim Botnet Attempting to Break into WordPress Sites’ Admin Accounts
A new Go-based botnet dubbed GoTrim has been identified scanning and brute-forcing self-hosted websites using the WordPress content management system (CMS) to seize control of targeted systems. The active campaign, observed since September 2022, utilises a bot network to perform distributed brute-force attacks in an attempt to login to the targeted web server.
Once broken in the operator proceeds by installing a downloader PHP script in the newly compromised host that deploys the bot client from a hard-coded URL, effectively adding the machine to the growing network. GoTrim does not have self-propagation capabilities of its own or have the ability to distribute other malware or maintain persistence in the infected system. The purpose of the malware is to receive further commands from an actor-controlled server that include conducting brute-force attacks against WordPress and OpenCart using a set of provided credentials.
GoTrim can alternatively function in a server mode where it starts a server to listen for incoming requests sent by the threat actor through the command-and-control (C2) server. This, however, only occurs when the breached system is directly connected to the Internet.
Another key feature of the botnet malware is its ability to mimic legitimate requests from the Mozilla Firefox browser on 64-bit Windows to bypass anti-bot protections, in addition to solving CAPTCHA barriers present in WordPress sites.
Source – https://thehackernews.com/2022/12/new-gotrim-botnet-attempting-to-break.html
FBI seized domains linked to 48 DDoS-for-hire service platforms
48 Internet domains have been seized and six suspects charged by the US Department of Justice for their involvement in running Booter or Stresser platforms that allow anyone to easily conduct distributed denial of service attacks.
Booters are online platforms allowing threat actors to pay for distributed denial-of-service attacks on websites and Internet-connected devices. Essentially, they are “booting” the target off of the Internet. Stressers offer the same DDoS features but claim to be provided for legitimate testing of the reliability of web services and the servers behind them. To use these services, threat actors register an account and deposit cryptocurrency, which is then used to pay for the services. While almost all booter/stresser sites require a subscriber to agree not to use the services to conduct attacks, many of these services are promoted on hacker forums and criminal marketplaces. In many cases, the platforms’ owners themselves promote deals and coupons on cybercrime sites or use affiliates who earn commissions for promoting the service.
The six suspects charged include a person from Texas, three from Florida, one from New York, and another from Hawaii who allegedly operated various stressor/booter sites, including RoyalStresser.com, SecurityTeam.io, Astrostress.com, Booter.sx, Ipstressor.com, and TrueSecurityServices.io. As part of a more extensive operation against DDoS platforms, dubbed Operation PowerOFF, the FBI and international law enforcement are seizing 48 Internet (complete list at the end of article) for stressor and booter platforms worldwide.
Fortinet Warns of Active Exploitation of New SSL-VPN Pre-auth RCE Vulnerability
Fortinet have issued emergency patches for a severe security flaw affecting its FortiOS SSL-VPN product that it said is being actively exploited in the wild. Tracked as CVE-2022-42475 (CVSS score: 9.3), the critical bug relates to a heap-based buffer overflow vulnerability that could allow an unauthenticated attacker to execute arbitrary code via specially crafted requests.
The following products are impacted by the issue –
• FortiOS version 7.2.0 through 7.2.2
• FortiOS version 7.0.0 through 7.0.8
• FortiOS version 6.4.0 through 6.4.10
• FortiOS version 6.2.0 through 6.2.11
• FortiOS-6K7K version 7.0.0 through 7.0.7
• FortiOS-6K7K version 6.4.0 through 6.4.9
• FortiOS-6K7K version 6.2.0 through 6.2.11
• FortiOS-6K7K version 6.0.0 through 6.0.14
Patches are available in FortiOS versions 7.2.3, 7.0.9, 6.4.11, and 6.2.12 as well as FortiOS-6K7K versions 7.0.8, 6.4.10, 6.2.12, and 6.0.15.
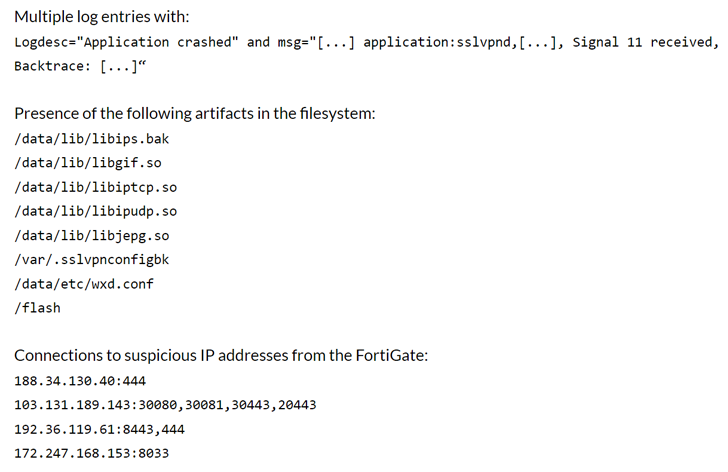
The American network security company has also published indicators of compromise (IoCs) associated with the exploitation attempts, including the IP addresses and the artifacts that are present in the file system post a successful attack.
Source – https://thehackernews.com/2022/12/fortinet-warns-of-active-exploitation.html
Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
An active malware campaign is targeting the Python Package Index (PyPI) and npm repositories for Python and JavaScript with typosquatted and fake modules that deploy a ransomware strain, marking the latest security issue to affect software supply chains.
The typosquatted Python packages all impersonate the popular requests library. According to Phylum, the rogue packages embed source code that retrieves a Golang-based ransomware binary from a remote server depending on the victim’s operating system and microarchitecture.
Successful execution causes the victim’s desktop background to be changed to an actor-controlled image that claims to the U.S. Central Intelligence Agency (CIA). It’s also designed to encrypt files and demand a $100 ransom in cryptocurrency. In a sign that the attack is not limited to PyPI, the adversary has been spotted publishing five different modules in npm: discordallintsbot, discordselfbot16, discord-all-intents-bot, discors.jd, and telnservrr.
The findings come as 10 additional PyPI packages were identified pushing modified versions of the W4SP Stealer malware as part of an ongoing supply chain attack aimed at software developers that’s believed to have started around September 25, 2022. Similarly, earlier this month new attack technique was demonstrated against a Rust repository (“rust-lang”) that abuses GitHub Actions to poison legitimate artifacts. Build artifacts are the files created by the build process, such as distribution packages, WAR files, logs, and reports. By replacing the actual modules with trojanised versions, an actor could steal sensitive information or deliver additional payloads to all its downstream users.
Source – https://thehackernews.com/2022/12/malware-strains-targeting-python-and.html
Most apps used in US classrooms share students’ personal data with advertisers
A new study has revealed that 96% of the apps used in U.S. K-12 schools share children’s personal information with third parties, including advertisers, often without the knowledge or consent of users or schools.
Researchers looked at 13 schools in every state, leading to a total of 663 schools representing nearly half a million students. They found that most schools had more than 150 approved technologies for classrooms with one school having as many as 1,411. The report highlights that the exposure of student data to advertisers through school-approved technology is a widespread problem. Nearly a quarter of the apps recommended or required by schools included ads and 13% included retargeting ads, which allow digital advertisers to pinpoint visitors based on previous website visits.
The use of education technology providers exploded when the COVID-19 pandemic forced classes online. But the quick adoption also meant that many school districts entered into agreements without much scrutiny or public discussion. One factor driving the data collection is that many of the technologies approved by schools for student use were not designed specifically for educational purposes — and in many cases not designed with children in mind. Such apps included The New York Times app, Duolingo and Amazon shopping.
Google was the most common third-party that received data from the apps used in schools. Nearly 70% of all apps were observed sending data to Google and 70% included Google software developer kits, an internal software component. Some of this is driven in part by Google’s dominance as a hardware and software supplier for K-12 schools thanks to the ubiquity of Google Classroom.
Customised apps for schools tended to be less safe than the general pool of apps studied, researchers found. For instance, researchers found that 81% of custom apps requested access to location information, a slightly larger number than 79% of all apps requesting that information. And 69% of custom apps accessed “social information,” such as calendars and contacts.
Recently regulators and privacy experts have begun to push back against the ed tech industry’s surveillance tactics.
Source – https://www.cyberscoop.com/apps-expose-student-data-privacy/
LockBit ransomware crew claims attack on California Department of Finance
Notorious and prolific ransomware operation Lockbit have claimed to have stolen 76 gigabytes of data from the California Department of Finance. In a statement on its website posted early Monday, LockBit announced that it targeted systems belonging to the California Department of Finance and gave the agency a Dec. 24 deadline, when the group is threatening that it will publish the stolen files.
The group claims that its haul of stolen data includes databases, confidential data, financial documents and sexual proceedings in court. The group posted seven screenshots of what appear to be budget documents, an old contract, and a screenshot from a file directory showing multiple other document folders — dated Dec. 7 and Dec. 8 — totaling 75.7 gigabytes. The group’s ransom demands are not clear.
The California Governor’s Office of Emergency Services said in a statement that the California Cybersecurity Integration Center (Cal-CSIC) is “actively responding to a cybersecurity incident involving the California Department of Finance.” The statement noted that “no state funds have been compromised,” but did not address whether records were accessed and, if so, which ones.
Source – https://www.cyberscoop.com/lockbit-ransomware-california-department-of-finance/
Uber suffers new data breach after attack on vendor, info leaked online
Uber has suffered a new data breach after a threat actor leaked employee email addresses, corporate reports, and IT asset information stolen from a third-party vendor in a cybersecurity incident. Early Saturday morning, a threat actor named ‘UberLeaks’ began leaking data they claimed was stolen from Uber and Uber Eats on a hacking forum known for publishing data breaches.
The leaked data includes numerous archives claiming to be source code associated with mobile device management platforms (MDM) used by Uber and Uber Eats and third-party vendor services. The threat actor created four separate topics, allegedly for Uber MDM at uberhub.uberinternal.com and Uber Eats MDM, and the third-party Teqtivity MDM and TripActions MDM platforms. Each post refers to a member of the Lapsus$ hacking group who is believed to be responsible for numerous high-profile attacks, including a September cyberattack on Uber where threat actors gained access to the internal network and the company’s Slack server.
The newly leaked data reportedly consists of source code, IT asset management reports, data destruction reports, Windows domain login names and email addresses, and other corporate information. One of the documents includes email addresses and Windows Active Directory information for over 77,000 Uber employees. The leaked data is thought to be related to internal Uber corporate information and does not include any of its customers. However, the data contains enough detailed information to conduct targeted phishing attacks on Uber employees to acquire more sensitive information, such as login credentials.
Uber has shared that threat actors stole its data in a recent breach on Teqtivity, which it uses for asset management and tracking services. A Teqtivity data breach notification published this week explains that a threat actor gained access to a Teqtivity AWS backup server that stores data for its customers. This allowed the threat actor to access information for companies using their platform such as makes, models and serial numbers of devices used as well as user information such as names and email addresses.
The source code leaked on the hacking forum was created by Teqtivity to manage Uber’s services, explaining the many references to the ride-sharing company. Uber has also reiterated that the Lapsus$ group was not related to this breach, even though the forum posts reference one of the threat actors associated with the group.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.