Friday, March 27th, 2020
Cybercrime in the time of COVID-19

Updated 15th May 2020
Over the past few months we have been witnessing an increased amount of malicious attempts as many threat actors have started to abuse the panic and discomfort of the COVID-19 pandemic to conduct specially crafted cyber attacks. Our SOCs are continually seeing a significant spike in activity on Brute-Force attacks (authentication issues), attempts for exploits (viruses) and increased access to malicious / suspicious IPs / URLs. We have also been monitoring a few forum sites on the dark web to understand whether discussions of COVID-19 are as popular there as they are on the clear web and what exactly cyber criminals are discussing about COVID-19. An interesting element that we found is a thread on encouraging users to do more ‘carding’ due to COVID-19. Their explanation? Due to COVID-19, cardholders are loading more money onto their bank accounts so that means that this a good period to do more carding.
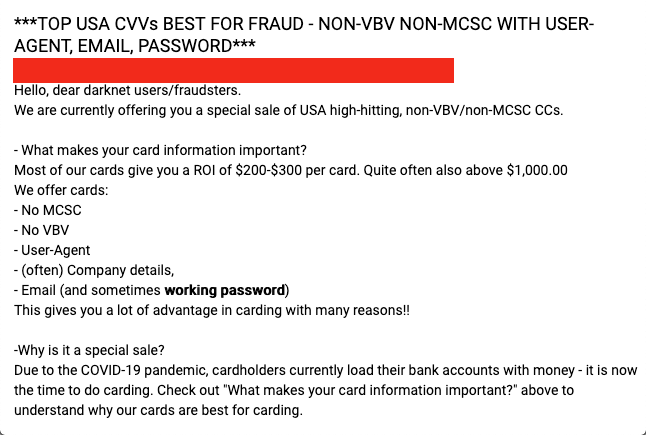
Others are simply just reassuring their clients that they’re ‘still delivering despite COVID-19’ or that they ‘have limited delivery options due to COVID-19’. There are also numerous ‘sale offers’ due to COVID-19. Needless to say, cyber criminals are readjusting their business models too.
Email is the largest threat vector of attack so it comes as no surprise that cybercriminals are launching phishing campaigns related to COVID19. Many of the emails, purportedly from official organisations, contain updates and recommendations connected to COVID19. Like most email spam attacks, they also include malicious attachments.
Here is a list of the most notable recent COVID19-themed malicious campaigns:
Phishing Emails
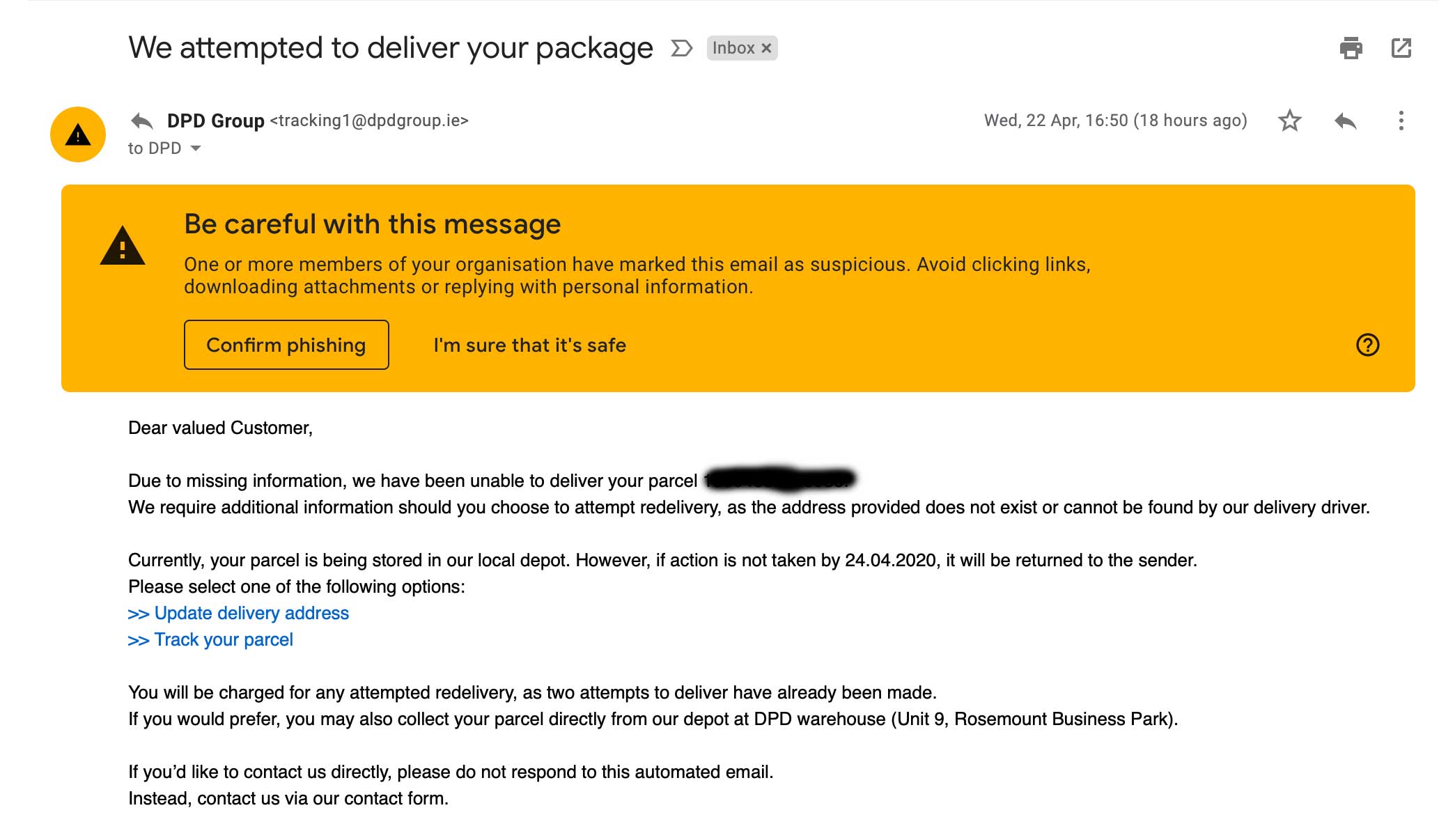
Example 1: Courier Group Scam emails
There are many scam campaigns which are targeting all of us, outside of the work environment. Hackers are now taking advantage of the increased amount of online deliveries which are taking place. This sample email below is claiming to be from the courier company, DPD informing customers that their delivery of goods has failed. The hackers here are simply wanting you to click on the links to infect your device with Malware.
Example 2: Spear- Phishing Campaign
FortiGuard Labs recently discovered a new COVID-19 related themed spear phishing email. The email was sent from [159.69.16[.]177] but claims to be from the World Health Organization (WHO).
The body of the email contains multiple points about infection control and other suggestions and recommendations, which is obviously a lure to further compel the recipient to continue reading. And in a twisted fashion, the messaging pretends to address misinformation related to COVID-19. Although the document appears to be written by someone who has a good grasp of English, there are some obvious grammatical, punctuation, and spelling issues that lead us to believe that English is likely the second language of the author.

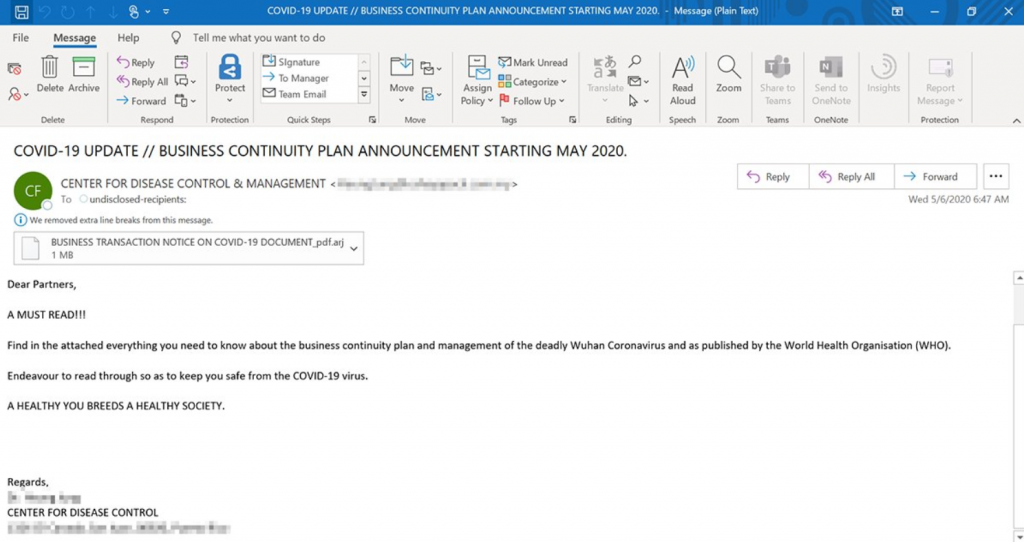
Example 3 – Email targeting Microsoft employees
Recent campaigns that deliver Lokibot, one of the first malware families to use COVID-19 lures which we saw also in our last blog examples, are showing a slight shift in tone reflecting current conversations, with subject lines like “BUSINESS CONTINUITY PLAN ANNOUNCEMENT STARTING MAY 2020”
The phishing emails contain malicious attachments that, if opened, enabled macros that install the LokiBot information stealer, according to Microsoft.
Android Spyware
A new prevalent example of Android Spyware that leverages COVID-19 as a way to deliver their malicious product has been reported by researchers at Lookout. This particular malware, called “corona live 1.1.”, comes out of Libya and seems to mostly be targeting Libyan citizens. Like other examples listed below, it uses the same COVID-19 dashboard developed by Johns Hopkins University.
AzorUlt Trojan
Malwarebytes Labs reported finding variations of an AzorUlt trojan malware embedded in some of these attachments. The AzorUlt trojan is a flexible type of malware that commonly collects important data like browser history, passwords, and session cookies from the infected computer, then sends that to a command and control server elsewhere online. From there it could download and execute more malicious code, such as ransomware. This particular type of trojan is good at staying hidden, as its core function is to collect vital data from non-persistent memory on the infected machine, then quietly deliver that to its command and control server.
Krebs On Security recently documented that some phishing campaigns use a live interactive map of COVID-19 to distribute different variations of the same AzorUlt trojan. The map and interactive dashboard were developed by Johns Hopkins University, so visually these emails could appear valid and trustworthy even to a cautious eye.
Ransomware
Our partners at Trend Micro, analyzed a coronavirus-themed malicious HTA file, possibly from the SideWinder APT group. Based on the command and control infrastructure and its connection to the Pakistani army, it is likely that SideWinder is using the coronavirus as a lure. SideWinder is an active group known for targeting military entities; their last notable activity was in January when we found evidence that they were behind malicious apps found on Google Play.
This HTA file contained a pop-up PDF lure displaying clickbait titles and images of the Pakistan army. It was connected with to these malicious URLs (blocked by Trend Micro):
- hxxp[://www.d01fa[.net/plugins/16364/11542/true/true/
- hxxp[://www.d01fa[.net/cgi/8ee4d36866/16364/11542/58a3a04b/file.hta
- hxxps[://cloud-apt[.net/202/6eX0Z6GW9pNVk25yO0x7DqKJzaNm6LIRaR0GCukX/16364/11542/2a441439

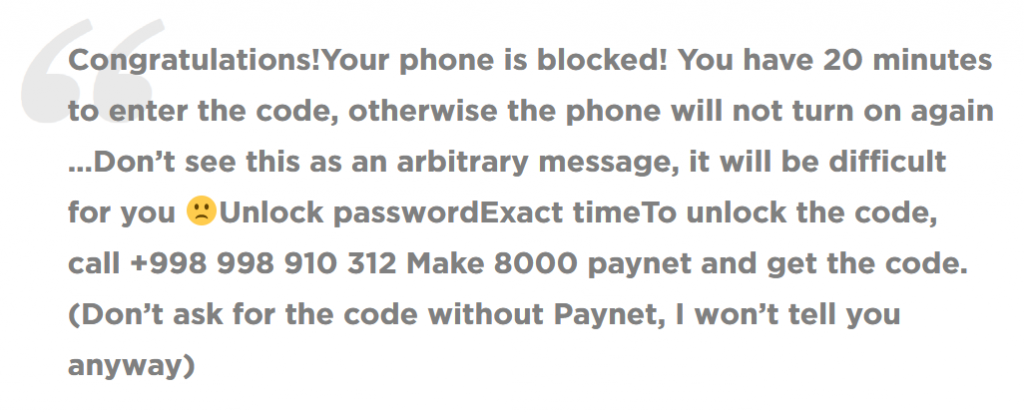
Cyber criminals are still taking advantage of the pandemic to spread ransomware, including on Android. In the last few weeks, we have observed multiple instances of the SLocker trojan. This is a very basic “locker” which masquerades as an informative application for Coronavirus. Once installed, the malicious application will block user activity, requesting payment (PayNet). When infected, users are met with the following (translated) message:
The example below was part of a widespread campaign used to spread Remcos RAT. (MITRE S0332). Remcos is a full-feature RAT capable of harvesting credentials, sensitive documents and information, as well as compromise basic functionality (keylogging, microphone access, screenshots, webcam control) and beyond. There are similar attacks focused on non-United States countries and financial entities as well
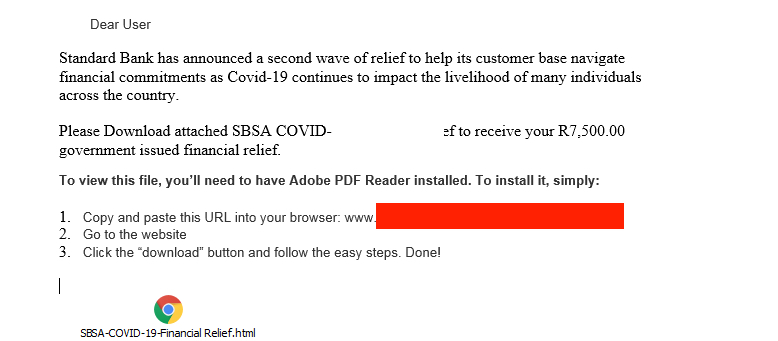
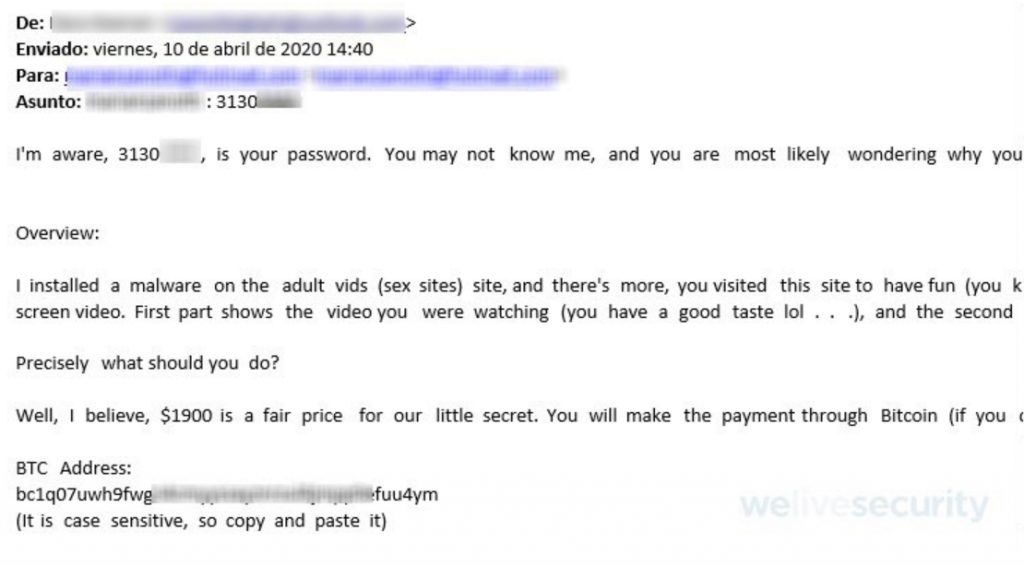
Sextortion Scam
In April, a new sextortion scam campaign was detected. The spam emails were detected by ESET’s research laboratory. They have been trying to trick victims by referring to old passwords. The hackers usually start with an alarming message about adult sites they may have visited and scare their potential victimsinto paying a sum of money within 24 hours or an embarrassing video will be released. They usually want the payment to be made in bitcoin.
Conclusion & Tips
It is very important to stay vigilant during this Covid-19 crisis. Ensure you have the relevant steps in place to manage any potential threats. Check your organisational security policies and procedures to ensure that your systems, devices and networks have the appropriate safeguards in place.
Be sure to only use trusted information sources from government and research institution’s websites. Don’t click on anything in your emails that’s health related. In general, be sure to follow all of the basic phishing recommendations. Be aware that people are trying to capitalise on fear.
Make sure your devices have the latest security updates installed and an antivirus or anti-malware service.
Use multi-factor authentication (MFA) on all your accounts. Most online services now provide a way to use your mobile device to protect your accounts in this way.
Educate yourself, friends, and colleagues on how to recognise phishing attempts and report suspected encounters. If you are an employer, now is the time to kick off that online security awareness campaign. You may also consider running phishing simulations campaigns to test your users’ current knowledge.
Our security teams at Smarttech247 are working to protect customers and we’ll share more in the coming weeks. For additional information and best practices for staying secure during these challenging times, please don’t hesitate to contact our experts. There is no cost and we are here to support you.
Stay safe.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.